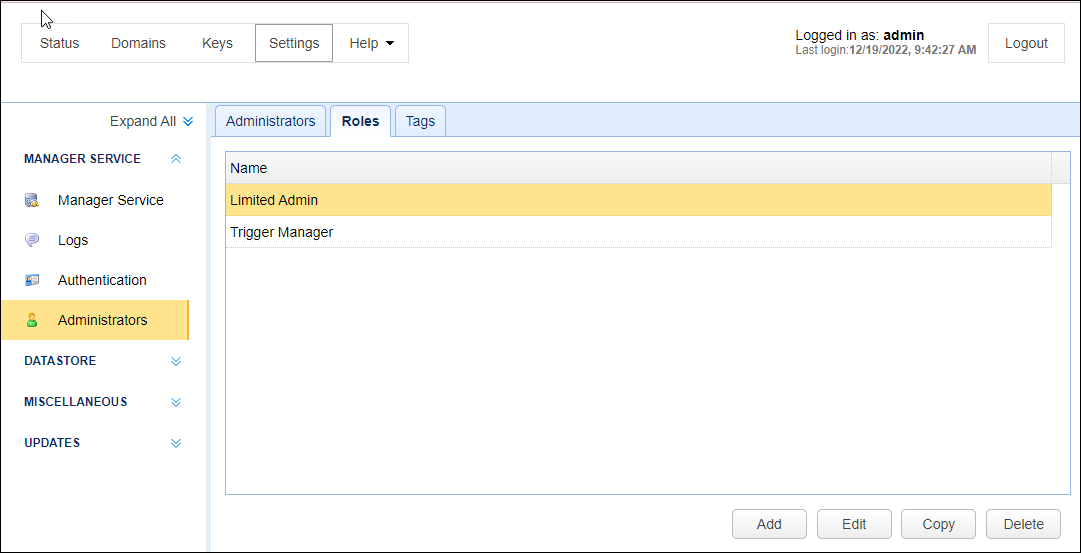
Administrative roles are a way for you to restrict administrative access to areas of the application using domain, module and tagged data as criteria. For example, you may wish to create an administrative role that allows an administrator to only see Triggers for a specific domain. Another example might be an administrative role that limits the Users that an administrator can see to those tagged users within a specific geographic region. Administrative roles may be managed from the Settings > MANAGER SERVICE > Administrators > Roles tab in the administrative user interface.
Add - Click to add an administrative role (see Adding administrative roles)
Edit - Select an existing role and then click this button to edit that role
Copy - Select an existing role and then click this button to copy that role (see Copying administrative roles)
Delete - Select an existing role and then click this button to delete that role
Figure 199
To add a Role click on the Add button. The Add Role dialog will be displayed.
Figure 200
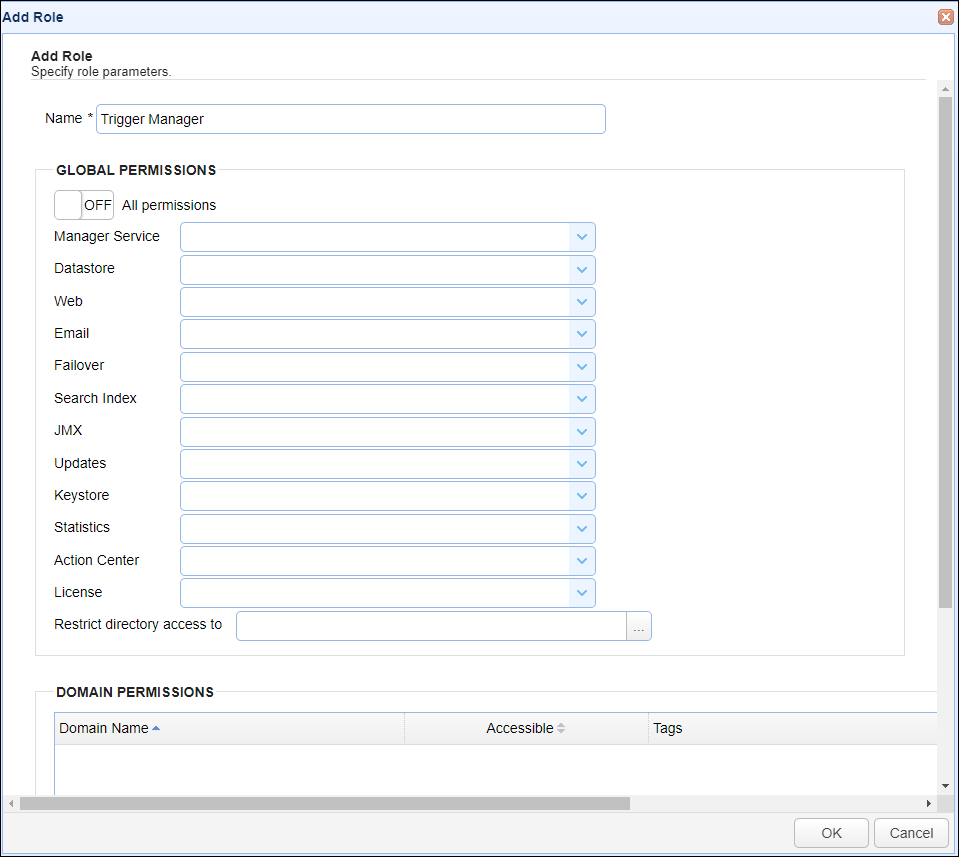
Name - The unique name to assign this role.
Global Permissions
Global permissions are those permissions which are not domain specific.
On/Off - By default, this toggle button is Off. When clicked, it is turned on. When turned on, all the Global permissions are applied to the role. When turned off, all Global permissions are removed.
Note: For each Global permission listed above (e.g. Manager service, Datastore, etc.), when you click on the permission's down arrow, you will see an option to Select all and Clear selection, designed to assist in the quick application or removal of permissions.
Manager Service - Defines whether administrators assigned to this role can Read/Write settings under Settings > MANAGER SERVICE.
Datastore - Defines whether administrators assigned to this role can Read/Write settings under Settings > DATASTORE.
Web - Defines whether administrators assigned to this role can Read/Write settings under Settings > MISCELLANEOUS > Web.
Email - Defines whether administrators assigned to this role can Read/Write settings under Settings > MISCELLANEOUS > Email.
Failover - Defines whether administrators assigned to this role can Read/Write settings under Settings > MISCELLANEOUS > Failover.
Search Index - Defines whether administrators assigned to this role can Read/Write settings under Settings > MISCELLANEOUS > Search Index.
JMX - Defines whether administrators assigned to this role can Read/Write settings under Settings > MISCELLANEOUS > JMX.
Updates - Defines whether administrators assigned to this role can Read/Write settings under Settings > UPDATES.
Keystore - Defines whether administrators assigned to this role can Read/Write settings under Keys.
Statistics - Defines whether administrators assigned to this role can read the Status information. If a role-based administrative user doesn't have Read permissions for this option, then information that relies on this access (e.g. Dashboard) will not be available, nor will that administrative user be able to access the RESTful API /management/server/statistics.
Action Center - Defines whether administrators assigned to this role can Read/Write settings under Status > Action Center.
License - Defines whether administrators assigned to this role have Read/Write access to License information. If Read is disabled (default), then read access to license information is restricted. If Write is disabled (default), then write access (ability to install license) is restricted. The Help > Install License menu item will not be visible if Write permissions is disabled.
Restrict directory access to - Defines what local directory administrators assigned this role can access, i.e. Read from or Write to, in the administrative interface. This includes directory paths used in AUTOMATION > Trigger actions, EDI > AS2 Messages > Send File, EDI> OFTP2 Messages > Send File, etc.
Domain Permissions
Domain permissions define those functions that an administrative user can perform for one or more domains. These permissions must be explicitly defined (i.e. if a role is not assigned permissions for a domain then administrative users assigned to that role will not be able to access that domain).
Figure 203
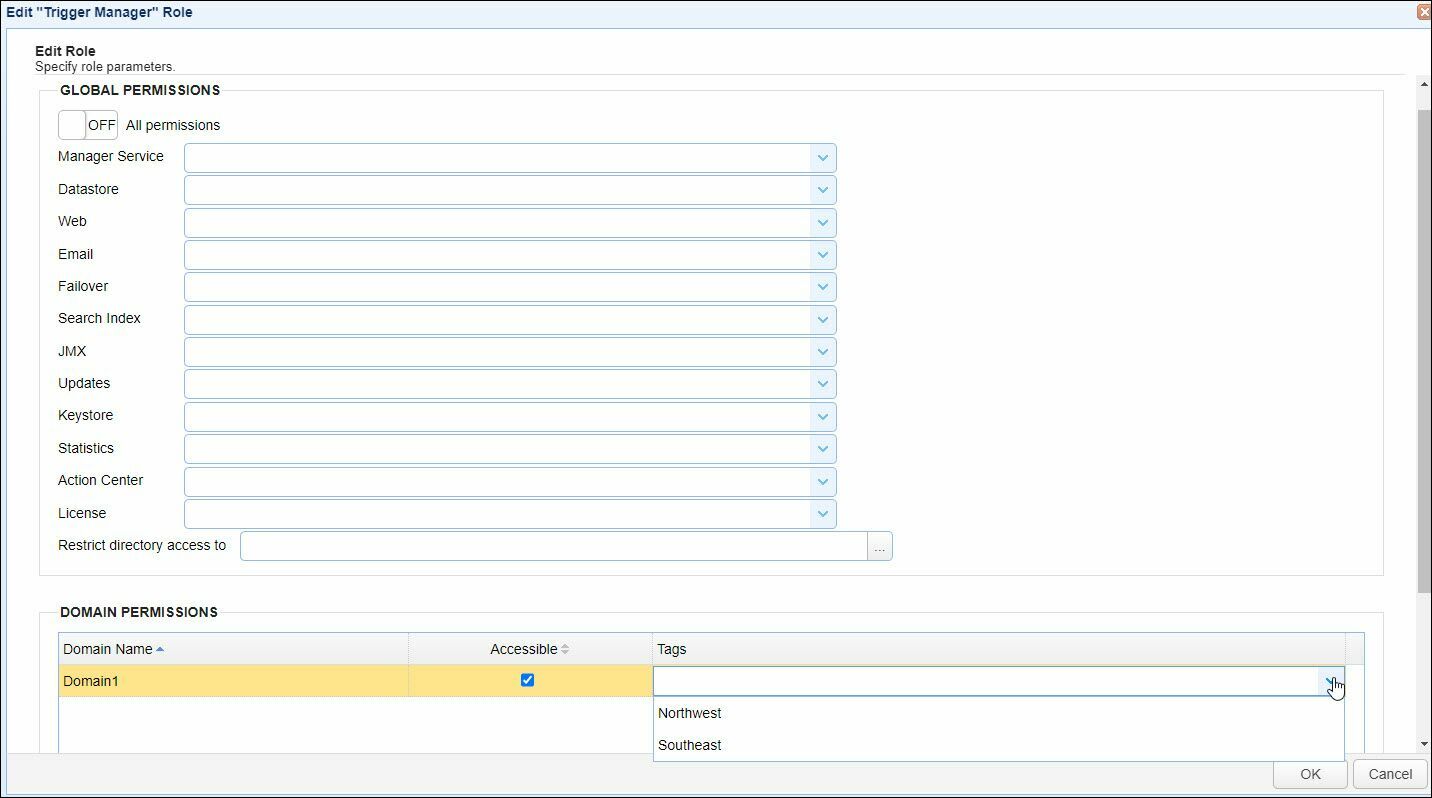
Domain Name - The domain these permissions apply to.
Accessible - Whether or not domain is accessible to role. Default is false.
Tags - Optional tags assigned to role. See Managing administrative tags.
To add domain permissions click the Add button. The Domain Access dialog will then be displayed.
Figure 201
Domain - The domain to add permissions for.
Once the domain has been added to the role you will then need to define permissions for that domain. To do this select the desired domain and click the Permissions button. The Domain Permissions dialog will then be displayed.
Figure 202
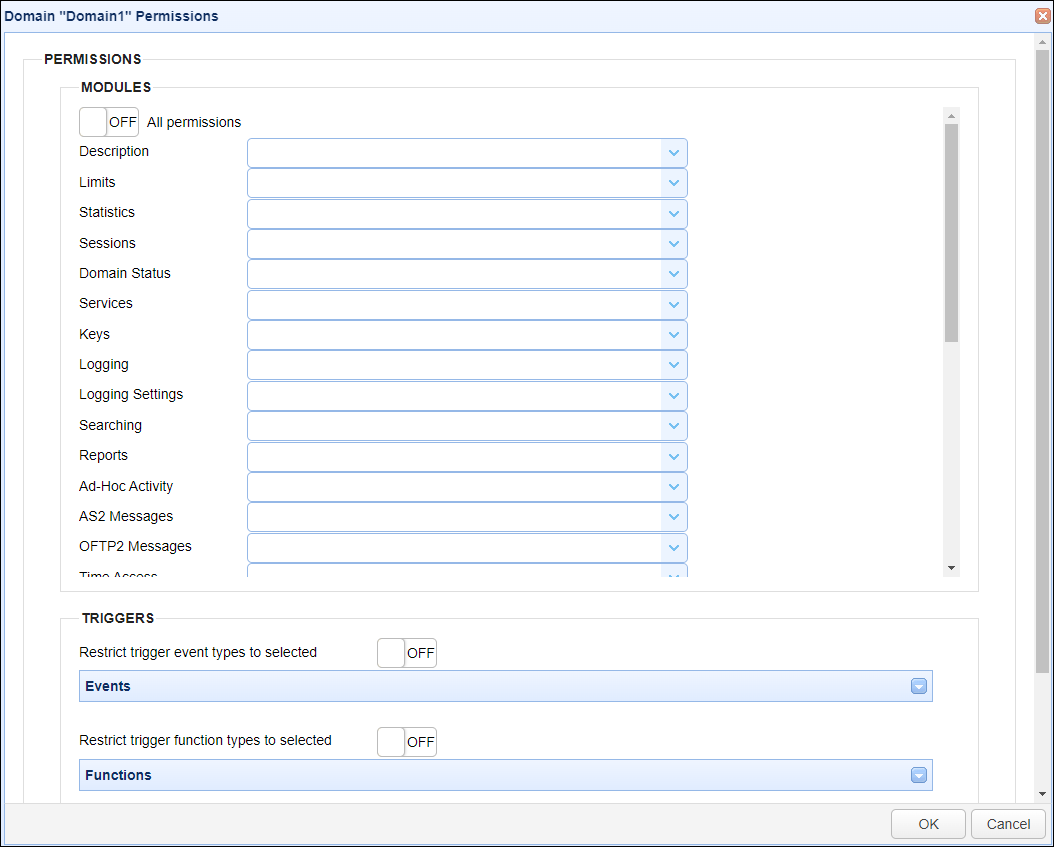
Permissions
On/Off - By default, this toggle button is Off. When clicked, it is turned on. When turned on, all the domain permissions are applied. When turned off, all domain permissions are removed.
Note: For each domain permission listed above (e.g. Description, Limits, etc.), when you click on the permission's down arrow, you will see an option to Select all and Clear selection, designed to assist in the quick application of permissions.
Description - Defines whether role has Read/Write permissions to the GENERAL > Overview > General > Description module for the domain.
Limits - Defines whether role has Read/Write permissions to the GENERAL > Overview > General > Limits module for the domain.
Statistics - Defines whether role has Read permission to the GENERAL > Overview > Statistics module for the domain.
Sessions - Defines whether role has Read/Write permissions to the GENERAL > Overview > Sessions module for the domain.
Domain Status - Defines whether role has ability to change status of the domain (start/stop/pause/resume/restart). This requires Write permission. The actions (start, stop, etc.) are accessible in the Domains module via buttons at the bottom of the Domains module, or when you right-click on a selected domain.
Services - Defines whether role has Read/Write permissions to the SERVICES > Listeners module for the domain.
Keys - Defines whether role has Read/Write permissions to the SECURITY > Keys module for the domain
Logging - Defines whether role has Read permission to the AUDIT > Logging module for the domain.
Logging Settings - Defines whether role has Read/Write permissions to the AUDIT > Logging > Settings module for the domain.
Searching - Defines whether role has Read/Write permissions to the AUDIT > Logging > Search module for the domain.
Reports - Defines whether role has Read/Write permissions to the AUDIT > Reports module for the domain.
AS2 Messages - Defines whether role has Read/Write permissions to the EDI > AS2 Messages module for the domain.
OFTP2 Messages - Defines whether role has Read/Write permissions to the EDI > OFTP2 Messages module for the domain.
Time Access - Defines whether role has Read/Write permissions to the SECURITY > Time Access module for the domain.
Banned Files - Defines whether role has Read/Write permissions to the SECURITY > Banned Files module for the domain.
Password Compliance - Defines whether role has Read/Write permissions to the SECURITY > Compliance module for the domain.
IP Access - Defines whether role has Read/Write permissions to the SECURITY > IP Access module for the domain.
DLP - Defines whether role has Read/Write permissions to the SECURITY > DLP Rules module for the domain.
Connections - Defines whether role has Read/Write permissions to the SERVICES > Connections module for the domain.
Triggers - Defines whether role has Read/Write/Run permissions to the AUTOMATION > Triggers module for the domain.
Authentication - Defines whether role has Read/Write permissions to the ACCOUNTS > Authentication module for the domain.
Accounts - Defines whether role has Read/Write permissions to the ACCOUNTS > Users module for the domain.
Groups - Defines whether role has Read/Write permissions to the ACCOUNTS > Groups module for the domain.
Network Storage - Defines whether role has Read/Write permissions to the ACCOUNTS > Network Storage module for the domain.
Directory Monitors - Defines whether role has Read/Write permissions to the AUTOMATION > Directory Monitors module for the domain.
Drop Zones - Defines whether role has Read/Write permissions to the SHARING > Drop Zones module for the domain.
URL Branding - Defines whether role has Read/Write permissions to the MISCELLANEOUS > URL Branding module for the domain.
Trading Partners - Defines whether role has Read/Write/Send permissions to the AUTOMATION > Trading Partners module for the domain.
Contacts - Defines whether role has Read/Write permissions to the SHARING > Contacts module for the domain.
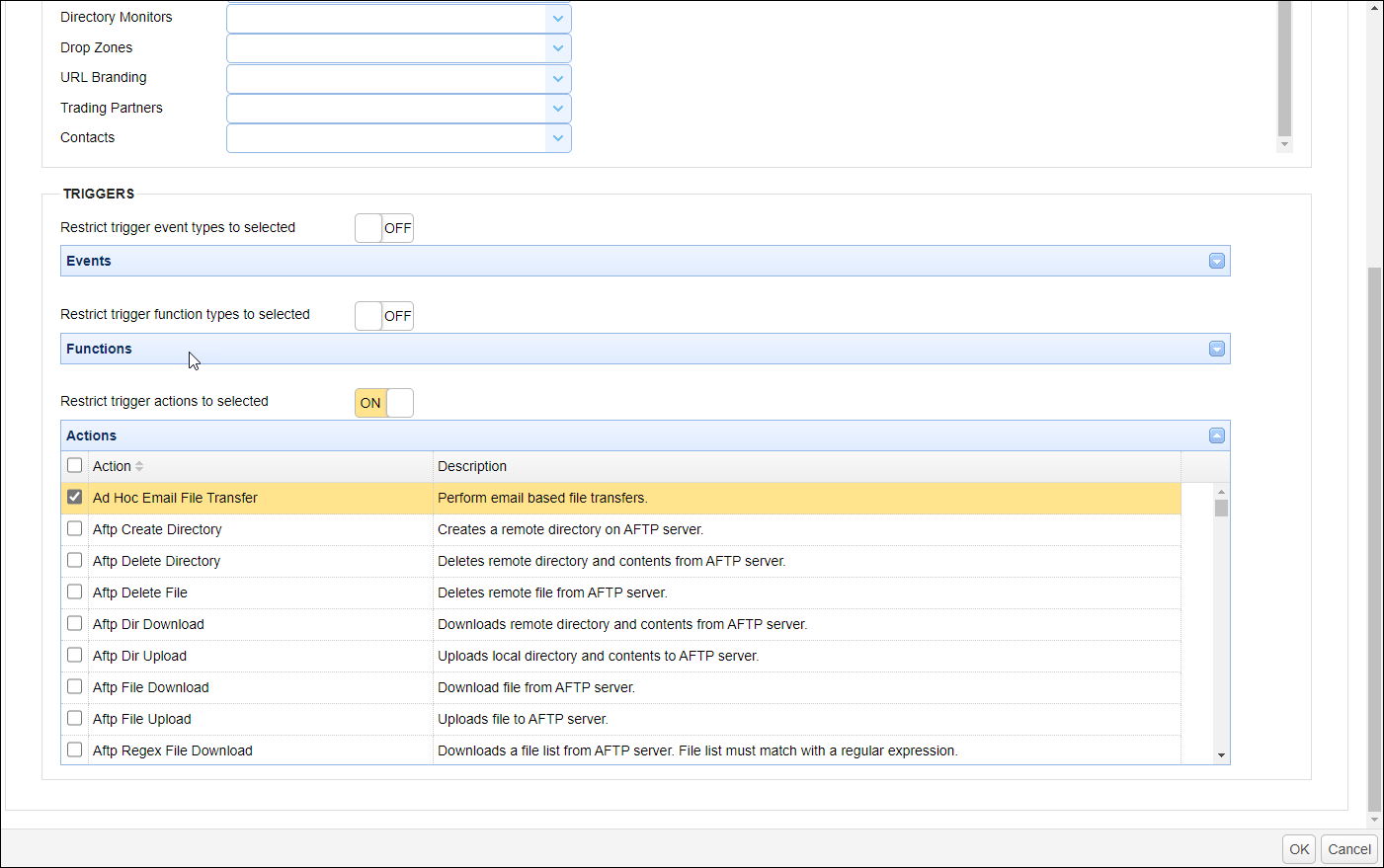
Restrict trigger event types to selected - When clicked from OFF to ON, you will be able to restrict access of this administrative role to specific trigger event types. You can specify which trigger event types will only be accessible to this administrative role by clicking the specific events in the list.
Restrict trigger function types to selected - When clicked from OFF to ON, you will be able to restrict access of this administrative role to specific trigger functions. You can specify which trigger functions will only be accessible to this administrative role by clicking the specific functions in the list.
Restrict trigger actions to selected - When clicked from OFF to ON, you will be able to restrict access of this administrative role to specific trigger actions. You can specify which trigger actions will only be accessible to this administrative role by clicking the specific actions in the list. .
The trigger event types, function types, and actions that are selected in their respective lists are the only events, functions, and actions that may be chosen by the administrative role in question when creating a trigger, whether via the GUI, API, or other tools.
Figure 298
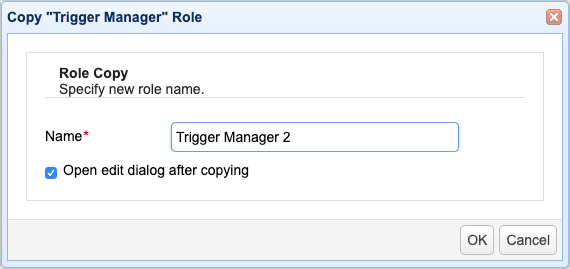
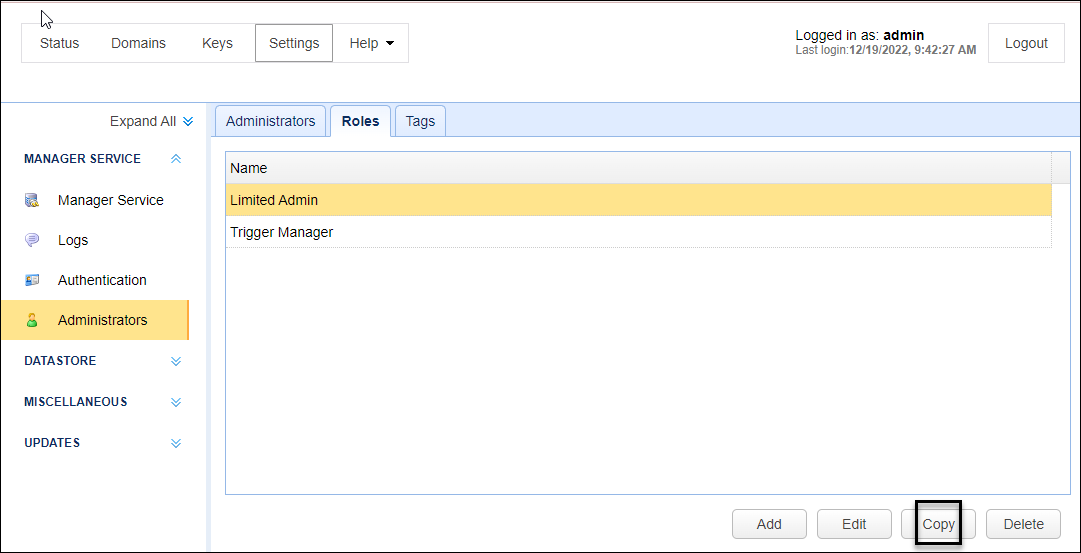
When creating an administrative role, it is often the case that the new role is just a slight modification of an existing role. To shorten the creation process of the new role, you may simply copy the definitions of that existing role. To do that, select the role you want to copy and click the Copy button, or right-click and select Copy from the pop-up menu.
Figure 333
Name - Enter the desired name for the new role into this field
Open edit dialog after copying - Leave this check box checked if you wish to review or edit the settings of the new role as soon as the copy completes.
Figure 334