You may be running JSCAPE MFT Gateway in an environment where FTP/S services listen on an internal address but are accessible to external users (e.g. via the Internet) using NAT (Network Address Translation).
For example, let's assume that your FTP reverse proxy service is listening on an internal IP address of 172.31.28.232 but is only accessible to external uses using the external IP address 200.200.200.200. When FTP/S clients connect to this FTP service and attempt to perform a directory listing or transfer a file a passive connection is typically used. In a passive connection the client sends the PASV command and the server responds with the IP address and port that the client should connect to perform the requested action. If the FTP reverse proxy service is listening on an internal IP address then it will return this IP address in it's response to the client.
Using the example IP addresses above, the problem here is that since 172.31.28.232 is an internal address it is non-routable to external users connecting over the Internet, likely resulting a connection timeout when the client tries to perform the requested action. To resolve this issue you must instruct JSCAPE MFT Gateway to use the passive IP address 200.200.200.200 rather than 172.31.28.232 when responding to passive requests. This can be achieved by navigating to the Services module in JSCAPE MFT Gateway Manager, selecting the FTP/S service whose passive IP address you wish to set, clicking the Edit button...
Figure 60
... navigating to the Advanced tab and then entering the desired value in the Passive IP field
Figure 31
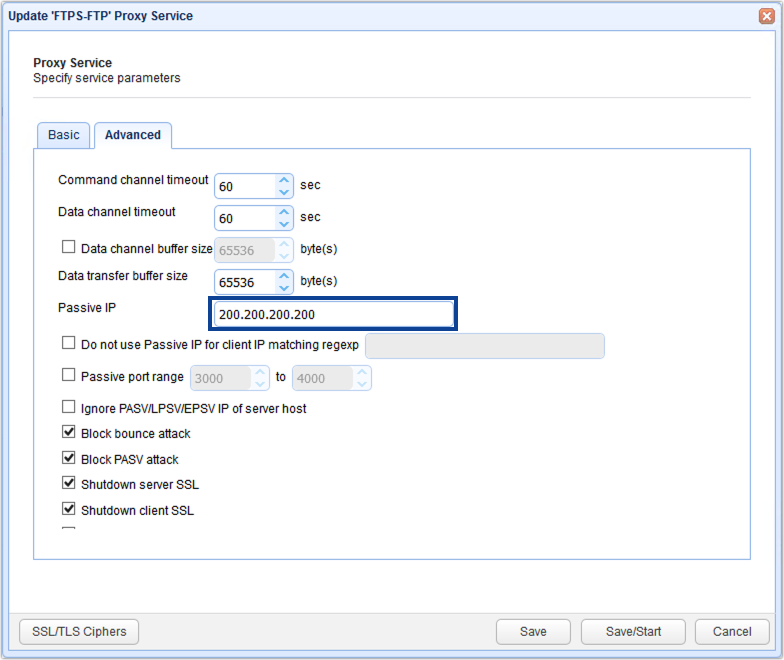
Command channel timeout - The time in seconds that a client may remain inactive on command channel before server forcefully disconnects client.
Data channel timeout - The time in seconds that a client may remain inactive on data channel before server forcefully disconnects client.
Passive IP - The IP address to use in response to passive client requests.
Do not use Passive IP for client IP matching regex - Passive IP will not be used for clients connecting from IP matching the specified regular expression. This is useful in cases where you do not want internal users to have passive connection re-routed to an external IP address.
Passive port range - The passive port range to use in response to passive client requests. If not enabled a random port range will be used. Ensure that this port range is open on any firewall that may be in front of the gateway.
Block bounce attack - If enabled FTP/S services will only be allowed to make PORT requests to originating host.
Block PASV attack - If enabled users will only be allowed to connect to passive data ports that are initiated by same client on command channel.
Shutdown server SSL for CCC command - If enabled server must properly shutdown SSL connections for command channel when issuing CCC command.
Shutdown client SSL for CCC command - If enabled client must properly shutdown SSL connections for command channel when issuing CCC command.
SSL/TLS Ciphers - The SSL/TLS ciphers enabled for FTP/S services.