In order to ensure interoperability with trading partners when using TLS to secure your OFTP data transfers, we suggest you take the following into consideration when generating server keys for your OFTP service.
Note: The cryptographic algorithms that will be used in OFTP TLS connections will require installation of the JCE Unlimited Strength Jurisdiction Policy Files, so we suggest you install those files first before generating your server keys.
Key lengths
Generate keys with long key lengths. Although 1024-bits is still the minimum recommended key length in the OFTP2 Implementation Guideline as of this writing, several businesses who are using OFTP have already started employing 2048-bit keys.
Figure 276
Server key Advanced Settings
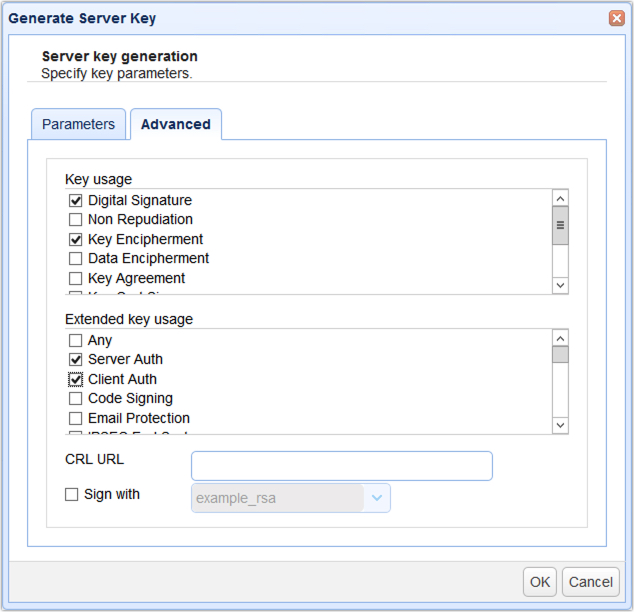
In OFTP, the certificate associated with the server key is normally used for the following purposes:
| • | digital signing |
| • | encryption |
| • | server authentication |
| • | client authentication |
You can specify how a certificate will be used by ticking the appropriate check boxes in the Advanced tab of the Generate Server Key dialog.
| • | Digital Signature - Check this if the certificate will be used for digital signing. |
| • | Key Encipherment - Check this if the certificate will be used for encryption |
| • | Server Auth - OFTP always requires server authentication, so this check box should be checked at all times. Otherwise, the certificate may be rejected by other OFTP hosts. |
| • | Client Auth - OFTP always requires client authentication, so this check box should be checked at all times. Otherwise, the certificate may be rejected by other OFTP hosts. |
If a certificate will be used for both digital signing and encryption, then both Digital Signature and Key Encipherment should be checked.
Figure 277