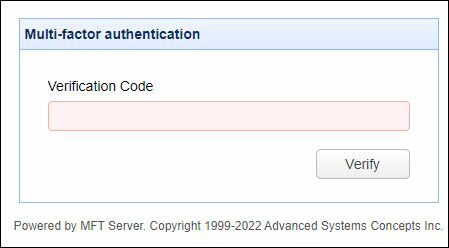
Multi-factor authentication (MFA) enables MFT Server to authenticate Administrators logging into the MFT Server Manager application using a Time-based, One-Time password form of authentication - in addition to the usual username and password.
To use the Time-based, One-time password, click on Settings > MANAGER SERVICE > Authentication > Multi-Factor Authentication, then select Time-based One-time Password. The only other option in the drop-down list is "none". Click Apply to confirm your selection.
Time-based, One-Time password (TOTP)
This enables MFT Server to authenticate Admins logging in to the MFT Server Manager by using the TOTP protocol.
How it works
1. Administrator logs in via the MFT Server Manager application.
Figure 391
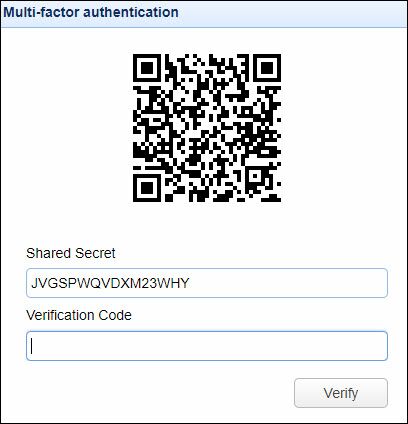
If TOTP is enabled (see Settings > MANAGER SERVICE > Authentication > Multi-Factor Authentication) AND the "Use multi-factor authentication" option is enabled for this particular Administrator (see Settings > MANAGER SERVICE > Administrators), AND a shared secret does not already exist for this account, then a QR code will be shown in the Admin's browser along with a shared secret key. Please note, you will also see the image below if you "Reset the TOTP Key", an option in the Administrator's Edit window.
Figure 392
2. Upon seeing the QRCode and secret key, the Admin either scans the QR code or manually types in the shared secret key into a TOTP app (e.g. GoogleAuthenticator). After which, the app should then generate a unique TOTP code (e.g. 137 821, as shown in Figure 393), which the Admin can then enter into the Verification Code field.
Here's an example of what will appear on the Google Authenticator mobile app:
Figure 393
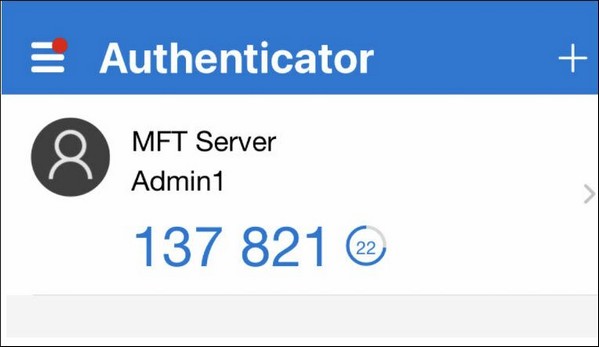
As its name implies, the time-based one-time password (TOTP) will only be valid up to a certain period of time (typically 30 seconds). Using the example in the above image, the clock is ticking down, and the Admin has 22 seconds left to enter the time-based, one-time password, until it resets. When that time expires, a new TOTP will automatically be generated. When logging in, the Admin should use the current TOTP. All previous TOTPs won't work.
3. In subsequent logins, the Admin will no longer have to scan the QR code or manually enter the shared secret key. All the Admin has to do is copy whatever TOTP is shown in the TOTP app and enter that into the Verification Code field, as depicted in the image below.
Figure 394