Information pertinent to a particular client key can be viewed by selecting the key and then clicking the View button. Note: The image below depicts using the key manager at the global level. The same steps apply when you access the key manager at the domain level via the SECURITY > Keys module.
Figure 273
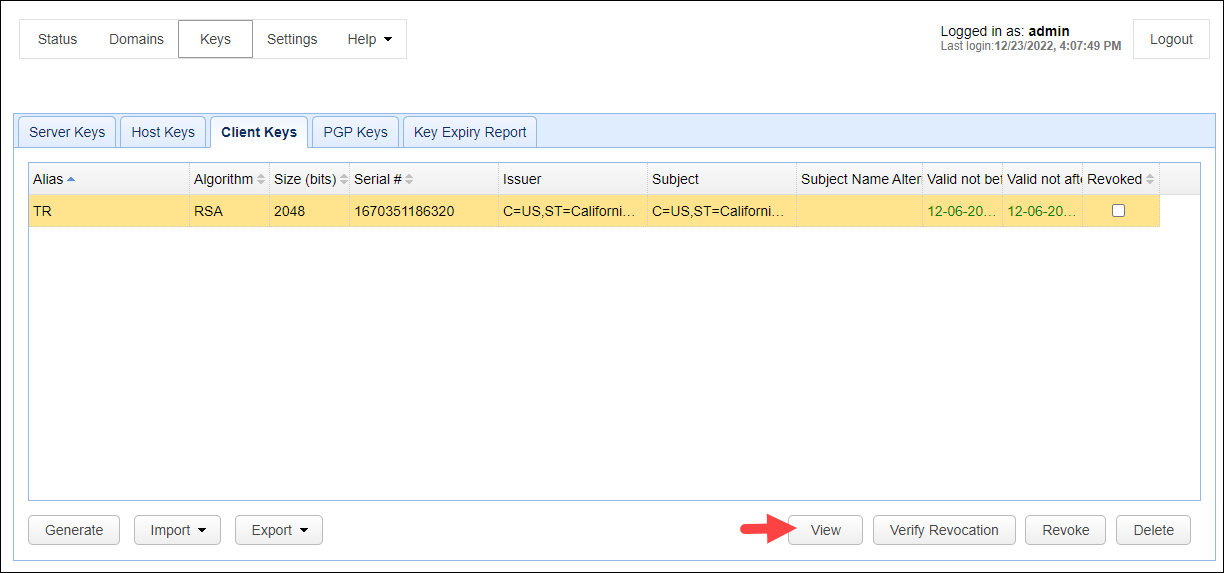
The information displayed will depend on the type of client key.
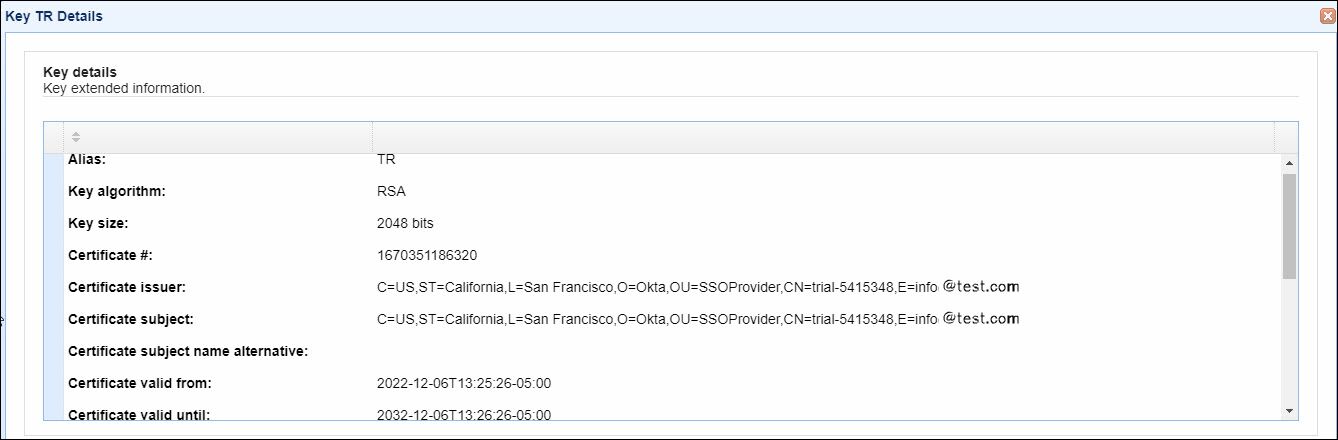
For client keys that contain a certificate, the following pieces of information are displayed:
| • | Alias - the name used to refer to this key in this MFT Server instance |
| • | Key algorithm - the key algorithm (e.g. RSA, DSA) |
| • | Key size - the length of the key (e.g. 1024, 2048, 4096) |
| • | Certificate number - the serial number of this certificate |
| • | Certificate issuer - information about the certificate authority (CA) who issued the digital certificate associated with this client key |
| • | Certificate subject - information about the owner of the digital certificate associated with this client key |
| • | Certificate valid from - indicates the start date when the certificate is deemed valid |
| • | Certificate valid until - indicates the end date up to which the certificate is deemed valid |
| • | Certificate expiration - the number of days until the certificate expires |
| • | Certificate signature - the digital signature associated with this digital certificate |
| • | Signature algorithm - the algorithm used to generate the digital signature |
| • | Key usages - the main uses of this key |
| • | Extended key usages - other uses of this key |
| • | Revoked - Indicates whether this key has been revoked or not |
| • | Revocation List URLs - URLs of revocation lists associated with this key |
Figure 274
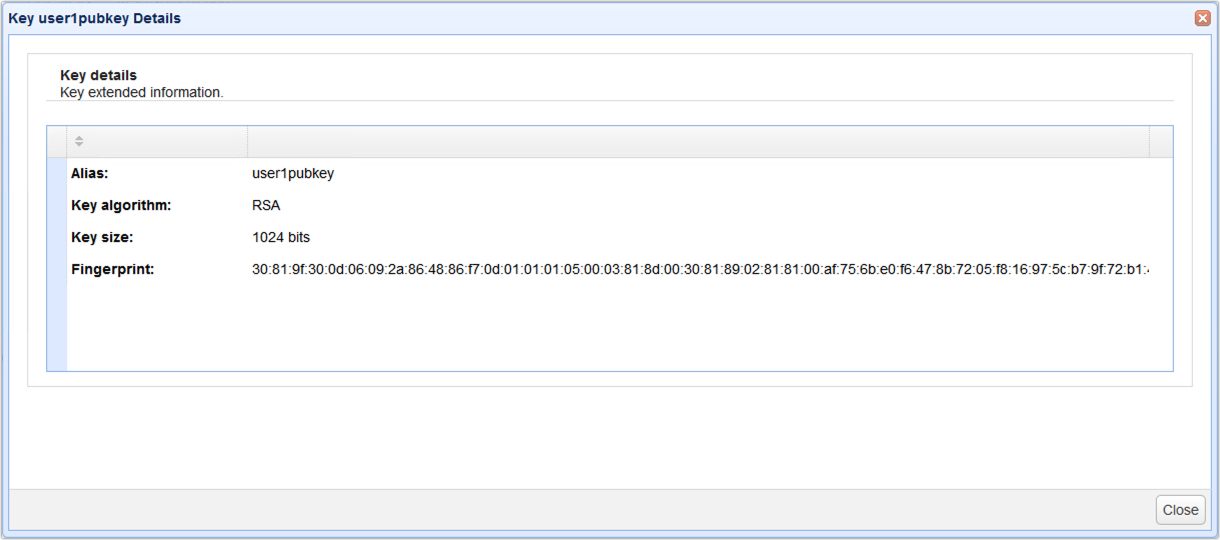
For public keys without a certificate, the following pieces of information are displayed:
| • | Alias - the name used to refer to this key in this MFT Server instance |
| • | Key algorithm - the key algorithm (e.g. RSA, DSA) |
| • | Key size - the length of the key (e.g. 1024, 2048, 4096) |
| • | Fingerprint - the fingerprint of this key. This can be particularly useful when you've just imported a client key from another party and you would like to verify the authenticity and source of the key (e.g. by verbally comparing with the key's sender) first before actually using it. |
Figure 275