The Compliance module contains several settings for meeting regulatory compliance requirements, particularly those pertaining to passwords, usernames, and allowed cryptographic algorithms.
JSCAPE MFT Server may be configured to require that user passwords meet certain requirements. To configure password requirements, click on the Compliance node in JSCAPE MFT Server Manager.
Figure 106
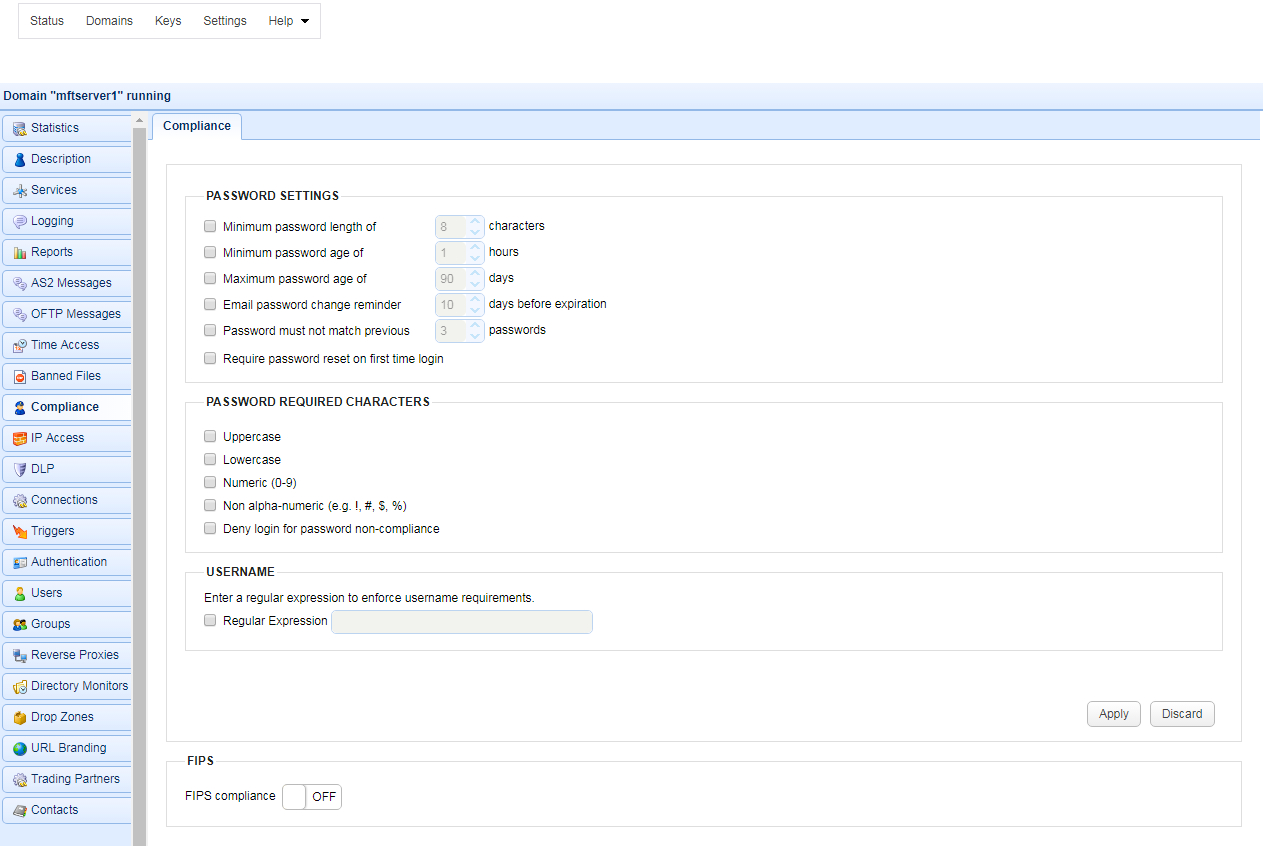
Minimum password length of - Requires that password contain the minimum number of defined characters.
Minimum password age of - Sets a minimum to the number of hours at which passwords may be changed. Administrators will be able to change passwords regardless of this setting.
Maximum password age of - Requires that user passwords be changed before reaching maximum password age. This option can be overridden at the user level by enabling the Ignore password aging rules option.
Email password change reminder - Emails a password change reminder to the email address associated with user the defined number of days before password reaches maximum password age. To function correctly an SMTP server must be configured under Settings > Email in JSCAPE MFT Server Manager. Note, email reminders are sent daily, approximately 10 minutes after start of JSCAPE MFT Server and every 24 hours thereafter.
Password must not match previous - Requires that new passwords must not match the defined number of previous passwords.
Require password reset on first time login - Requires new users to reset their passwords the first time they login.
Deny login for password non-compliance - If enabled, user password will be verified at time of login to check that it meets compliance requirements. If it matches user password but does not meet compliance requirements then user will be denied login.
Required characters - Passwords must contain the selected characters.
You may configure JSCAPE MFT Server to accept only a specific pattern for usernames by entering a regular expression.
FIPS compliance - If switched ON, administrators will not be allowed to change allowed ciphers, whether through the GUI or administrative API. This setting is ideal for environments that need to comply with regulations requiring 'strong cryptography'. Many of these regulations only allow cryptographic algorithms recommended by duly recognized standards such as the Federal Information Processing Standards (FIPS).
Prerequisites for using the FIPS compliance setting
Before the FIPS compliance settings can take effect, a couple of things need to be in place.
| • | The Bouncy Castle libraries (JAR files that begin with bc*) found in the 'libs' directory of the JSCAPE MFT Server installation directory need to be replaced with the libraries found in the 'fips' directory. Create backups of the original bc* files in case you might need them in the future. Once the said files have been replaced, JSCAPE MFT Server must be restarted for the changes to apply. |
| • | Some headless environments (namely Linux, CentOS, Ubunta) may suffer from slow-startup time due to entropy issues when using FIPS libraries. It is for this reason that FIPS related libraries were placed in a separate directory rather than including them in the default "libs" directory. A work-around for this issue is to install haveged to ensure that the entropy pool is more quickly populated in headless environments. (Read Installing haveged). |
Note: While non-shared services defined at domain level e.g. FTPS, SFTP etc. will adhere to the FIPS compliance settings mentioned above, shared services like HTTPS will not be able to do so. In order for your HTTPS services to adhere to FIPS compliance, you need to configure the FIPS settings in Settings > Web.
Note: RSA and DSA keys should be at least 2048 bits long for FIPS mode to work