A user is a valid account that may login to a domain's service. To view a list of users click on the Users node for the desired domain.
Figure 15
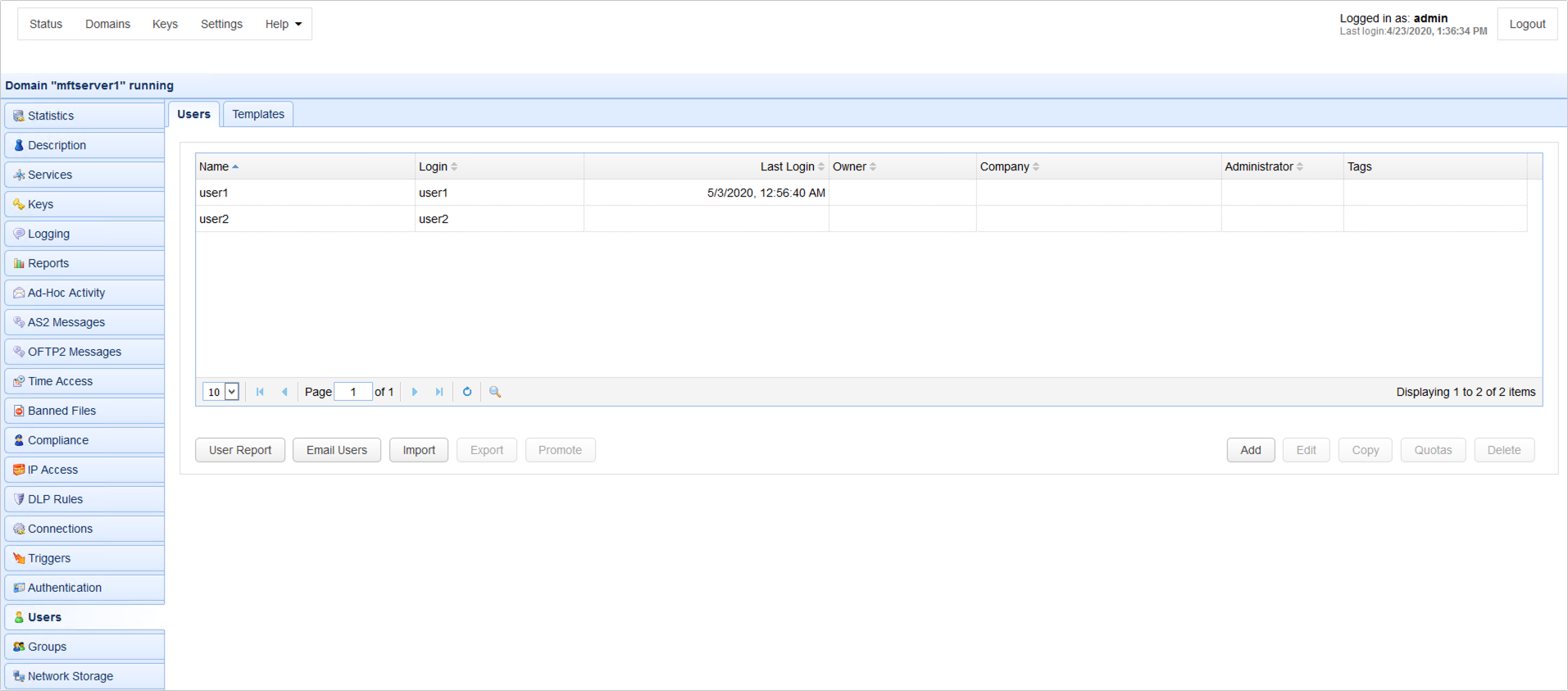
To add a user click on the Add button in the lower right corner. Choose a Template or accept the Default template and then click the OK button. The Add User dialog will be displayed.
Figure 16
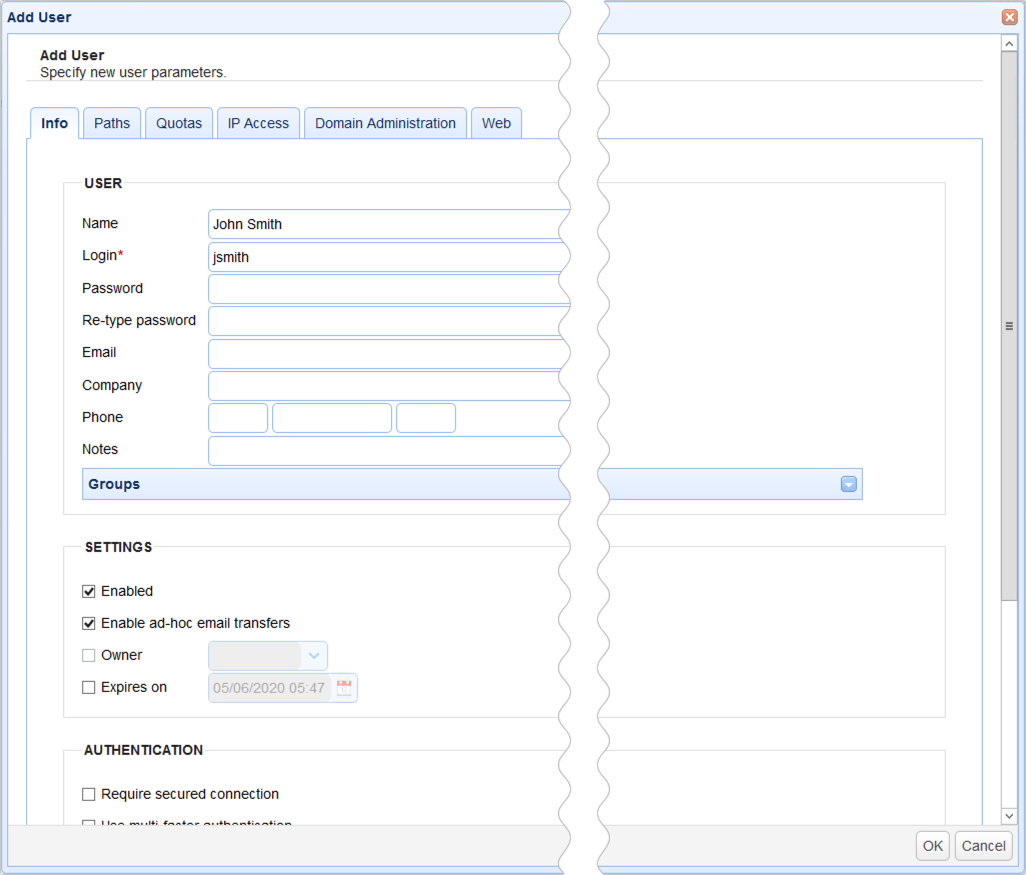
User
Name - The full name of this user.
Login - The login name for this user.
Password - The password for this user.
Re-type password - The password for this user.
Email - Optional email address for this user.
Company - The company that this user is associated with.
Phone - The phone number for this user. The first field is the country code (e.g. "1" for United States) and the second field is the telephone number including any area code, the third field is the phone extension. This field is used primarily in conjunction with Phone Authentication.
Notes - Use this field to enter internal owner information, user notes/descriptions, and just about any piece of relevant information that doesn't fall into any of the other fields provided
Groups - Optional groups that this user is a member of.
Settings
Enabled - Check to enable this account.
Enable ad-hoc email transfers - Check to allow user to perform ad-hoc email transfers via HTTP interface.
Owner - Optional login of user who owns/manages this account.
Expires on - Date that this account expires (leave blank for non-expiring account).
Authentication
Require secured connection - Check to force user to login using secure protocol (e.g. FTPS/SFTP/HTTPS).
Use two-factor phone authentication - Check to require user to use two-factor phone authentication.
Allow password change - Check to allow user to change their password.
Ignore password aging rules - Check to disable password aging rules for this user.
Client keys - Optional public-keys bound to this user for purposes of public-key authentication in SFTP/SSH protocol, or client certificate authentication in SSL protocols.
Tags
Tags may be used to limit visibility of users to administrators that are assigned a role containing specified tag.
See also