Users may authenticate with JSCAPE MFT Server using a variety of different authentication protocols. To view the current authentication method used click on the "Authentication" node for the desired domain.
Domain User Authentication is the most basic form of authentication, authenticating against local user accounts created for the domain using JSCAPE MFT Server Manager.
Figure 58

Database User Authentication allows you to authenticate a user based on whether the user has credentials to connect to a database. When connecting to the supplied JDBC URL the username and password provided at time of login are used to login to the JDBC URL. If user authenticates successfully with the JDBC URL then user is considered a valid user of the JSCAPE MFT Server service.
Figure 59

JDBC URL - The JDBC URL used to connect to the database. The above example demonstrates connecting to a MySQL database. Contact your database vendor for access to JDBC libraries and assistance on specifying the JDBC URL. Libraries for JDBC drivers must be placed in the libs directory of your JSCAPE MFT Server installation, driver class registered under Server > Settings > JDBC and JSCAPE MFT Server Service restarted in order to be loaded.
Create account if not found using template - This allows for accounts to be created automatically upon successful authentication. If selected, an account will be created automatically (if it does not exist already) using the specified User Template.
Database Query Authentication allows you to authenticate a user based on the results of a database query. If one or more records are returned from the query then the user is successfully authenticated.
Figure 60

JDBC URL - The JDBC URL used to connect to the database. The above example demonstrates connecting to a MySQL database. Contact your database vendor for access to JDBC libraries and assistance on specifying the JDBC URL. Libraries for JDBC drivers must be placed in the libs directory of your JSCAPE MFT Server installation, driver class registered under Server > Settings > JDBC and JSCAPE MFT Server Service restarted in order to be loaded.
User - The username to connect with when authenticating with JDBC database.
Password - The password to connect with when authenticating with JDBC database.
SQL query - The query to perform to authenticate the user. There are two special variables that may be used when performing the database query %username% and %password% which refer the username and password passed in during the authentication process. Note: SQL queries and stored procedures may be used, however stored procedures which make use of output parameters MAY NOT be used. Variables %username% and %password% are treated as strings so MUST be enclosed in single quotes.
Hash password class - The Java class to use for hashing password before passing to SQL query. If no class is specified then password will be passed to SQL query in clear text.
Create account if not found using template - This allows for accounts to be created automatically upon successful authentication. If selected, an account will be created automatically (if it does not exist already) using the specified User Template.
See also
LDAP User Authentication allows you to authenticate a user based on whether the user has the credentials to connect to the LDAP or Active Directory service.
Figure 61

Host - The hostname or IP address of the LDAP service.
Port - The port of the LDAP service.
User DN - The users distinguished name for authenticating with the LDAP service. The variable %username% may be used which refers to the username passed in during the authentication process.
Use SSL connection - Connect to LDAP server using SSL connection.
Allow anonymous binding - Sets whether user can bind anonymously to LDAP directory.
Use failover server - If enabled and primary LDAP server is inaccessible then authentication will be attempted against failover server.
Create account if not found using template - This allows for accounts to be created automatically upon successful authentication. If selected, an account will be created automatically (if it does not exist already) using the specified User Template.
LDAP Query Authentication allows you to authenticate a user based on the results of a LDAP query. LDAP Query Authentication is a two step authentication process.
1.User is authenticated against LDAP server using the User DN field and the password supplied by user when authenticating against JSCAPE MFT Server file transfer service.
2.Query is performed using credentials supplied in Search User DN and Password fields. Note, these credentials MAY be different than the credentials used in step 1. For example, a case where these might be different is where the User DN does not have the needed permissions to perform the query but the Search User DN does.
If one or more records are returned from the query then the user is successfully authenticated.
Figure 62

Host - The hostname or IP address of the LDAP service.
Port - The port of the LDAP service.
User DN - The users distinguished name for authenticating with the LDAP service.
Search User DN - The user distinguished name used for performing LDAP search query.
Password - The user password for performing LDAP search query.
Base DN - The base distinguished name in which to perform the filter.
Filter - The filter to execute using the LDAP filter syntax. There are two special variables that may be used when performing the database query, %username% and %password% which refer the username and password passed in during the authentication process.
Hash password class - The Java class to use for hashing password before passing to filter. If no class is specified then password will be passed to filter in clear text.
Use SSL connection - Connect to LDAP server using SSL connection.
Use failover server - If enabled and primary LDAP server is inaccessible then authentication will be attempted against failover server.
Create account if not found using template - This allows for accounts to be created automatically upon successful authentication. If selected, an account will be created automatically (if it does not exist already) using the specified User Template.
See also
When using LDAP Query Authentication you must define a filter that will be used to identify the record you are searching for. The syntax of LDAP filters are defined in RFC 2254. The table below provides a list of valid expressions and their meanings.
Symbol |
Filter |
Example |
Example matches |
= |
Equality |
(sn=Smith) |
Surname of Smith only. |
> |
Greater than |
(sn>Smith) |
Any surname that alphabetically follows Smith. |
>= |
Greater than or equal to |
(sn>=Smith) |
Any surname that includes or alphabetically follows Smith. |
< |
Less than |
(sn<Smith) |
Any surname that alphabetically precedes Smith. |
<= |
Less than or equal to |
(sn<=Smith) |
Any surname that includes or alphabetically precedes Smith. |
=* |
Presence |
(sn=*) |
All surnames (all entries with the sn attribute). |
=* |
Substring |
(sn=Smi*) |
Any matching substring of Smith. |
& |
And |
(& (sn=Smith) (cn=John) ) |
Surname of Smith and common name of John. |
| |
Or |
(| (sn=Smith) (sn=Jones) ) |
Surname of Smith or Jones. |
! |
Not |
(! (sn=Smith)) |
Surname not equal to Smith. |
See also
Authenticating with Microsoft Active Directory
Using NTLM Authentication you may authenticate against an existing Windows user repository.
Figure 118

Host - The IP address of Windows domain controller.
Windows Domain - The name of the Windows domain to which users belong.
Create account if not found using template - This allows for accounts to be created automatically upon successful authentication. If selected, an account will be created automatically (if it does not exist already) using the specified User Template.
Using PAM Authentication you may authenticate against an existing UNIX PAM user repository. In order to use the PAM Authentication module you must install some native libraries that allow JSCAPE MFT Server to communicate with your PAM user repository.
1.Download the JPam library for your operating system.
2.Copy the native library to the Java Native Libary Path. See the Native Library Installation Location table for details. Note Step 1 in the JPam instructions should be ignored as the jpam.jar file already exists in the libs directory of your JSCAPE MFT Server installation. Additionally, JPam instructions state you may optionally place native library in same directory as the jpam.jar file instead of the Java Native Library Path. This is incorrect. For JPam to work with JSCAPE MFT Server you MUST place native library in the Java Native Library Path and NOT in the libs directory of JSCAPE MFT Server.
3.Configure JPam for use by editing the net-sf-jpam file and copying it to to /etc/pam.d directory.
4.Restart JSCAPE MFT Server Service and JSCAPE MFT Server Manager.
5.Using JSCAPE MFT Server Manager go to the "Authentication" panel and set the Service type to "PAM Authentication" and enable other options. See Figure 117.
6.Click "Test parameters" button to test.
Figure 117

Enable debug to file system_output.log - Sends debugging information to file system_output.log in installation directory.
Create account if not found using template - This allows for accounts to be created automatically upon successful authentication. If selected, an account will be created automatically (if it does not exist already) using the specified User Template.
Using Custom User Authentication you may define your own custom authentication class.
Figure 86

Authentication class - The custom authentication class name.
Create account if not found using template - This allows for accounts to be created automatically upon successful authentication. If selected, an account will be created automatically (if it does not exist already) using the specified User Template.
See also
Authenticating using custom authentication API
The Database Query Authentication and LDAP Query Authentication services both support optional password hashing. Many databases and LDAP repositories store passwords in a hashed format. This is a security measure used in order to protect user credentials should a database or LDAP repository be compromised. JSCAPE MFT Server includes some built-in classes that may be used for hashing a password before it is sent for authentication against a database or LDAP repository. These classes are com.jscape.inet.mft.authentication.MD5Hasher and com.jscape.inet.mft.authentication.SHA1Hasher which offer MD5 and SHA1 hashes respectively.
Note: The hashes provided by the MD5Hasher and SHA1Hasher classes are provided in lowercase format.
Some databases or LDAP repositories may store passwords in a salted hash format. In a salted hash format the password is combined with other data (the salt) prior to being hashed. Salted hash passwords are typically used in an effort to avoid brute-force password attacks should the database or LDAP repository be compromised. Password salting is generally application dependent, therefore should you need to use a salted password it is necessary to write your own password hasher using the JSCAPE MFT Server API. To implement your own password hashing provider you must perform the following:
1. Create a Java class which implements the com.jscape.inet.mft.authentication.Hasher class.
2. Overload the public String createHash(String login, String password) method, returning the hashed value.
3. Create a JAR file that contains the compiled version of your com.jscape.inet.mft.authentication.Hasher implementation. To compile your authentication class you will need to include the ftpserver.jar library in your classpath. The ftpserver.jar library may be found in the libs directory for JSCAPE MFT Server.
4. Place the JAR file created in step 3 into the libs directory of your JSCAPE MFT Server installation.
5. Shutdown any open instances of JSCAPE MFT Server Manager and restart the JSCAPE MFT Server Service.
6. In the "Hash password class" field of the "Database Query Authentication" service or "LDAP Query Authentication" service enter the full classname, including package name of your hash provider.
The Phone Authentication module in JSCAPE MFT Server provides tokenless two-factor authentication support for your user accounts. This is a very secure method of authenticating users in that it combines something users know (their username/password) with something they have (a telephone or cellphone). Using the Phone Authentication module ensures that even if a user's password is stolen their account cannot be compromised.
How it works
1.User authenticates with JSCAPE MFT Server service as normal.
2.User instantly receives a phone call from Two-Factor Authentication service asking user to confirm this is a valid login.
3.Upon confirmation, user is logged into their account.
Enabling Phone Authentication
1.Select the Two-Factor Authentication tab and select the authentication service you wish to use.
2.Enter details for service and click Apply.
3.Enable the "Use phone authentication" option for those user accounts that you want to use this service.
If you are using the PhoneFactor service you will need to first sign up for the PhoneFactor JSCAPE Edition. For additional information on PhoneFactor please visit http://www.phonefactor.com/jscape.
Figure 119

License directory - The directory containing your PhoneFactor SDK license and private key files.
Password - Your PhoneFactor account password. This password can be found in the private-key-password.txt file that was provided as part of the PhoneFactor download.
Allow international calls - If checked fee based calls may be made to areas outside of the free Global Services locations defined by PhoneFactor.
Figure 120
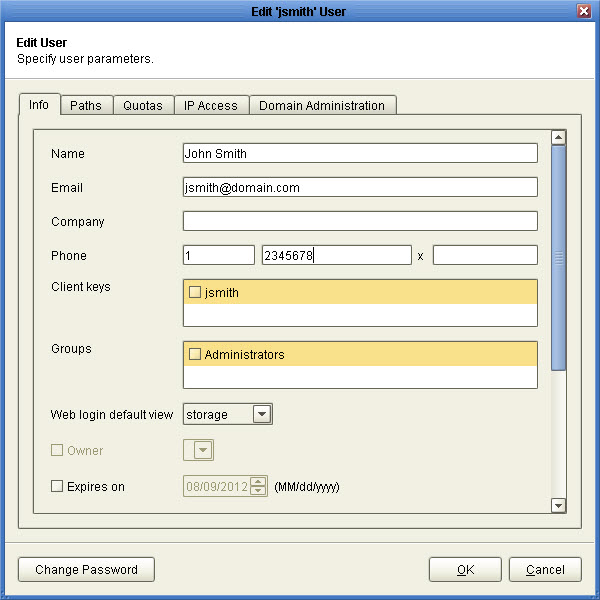
Note
Make sure that you enter the country code and phone number (including any area code) in the Phone field for your users using this service. The first field is your country code (1 for the United States), the second field is your phone number (including any area code), the third field is an optional extension. DO NOT include any non-numeric values in your phone number (e.g. hyphens, parenthesis etc.). This will be the number that is called when performing phone authentication.