This trading partner exchanges data with a remote SFTP or SCP service. The MFT Server initiates the connection to the remote SFTP or SCP service that you configure for this trading partner. It is assumed that the administrator of the remote service has provided you with the details needed to set up the SFTP or SCP trading partner - details such as the system's hostname or IP address, port number, username, password (if any), optional host key, and so on.
Adding the SFTP/SCP trading partner
In the desired domain, navigate to the AUTOMATION > Trading Partners module. Click on the Add button, or right click anywhere in the grid area and select Add from the pop-up menu. In the Add Trading Partner dialog window, select SFTP/SCP as the Protocol, then click OK. The Add "SFTP/SCP" Trading Partner dialog will appear as depicted in the figure below.
Figure 458
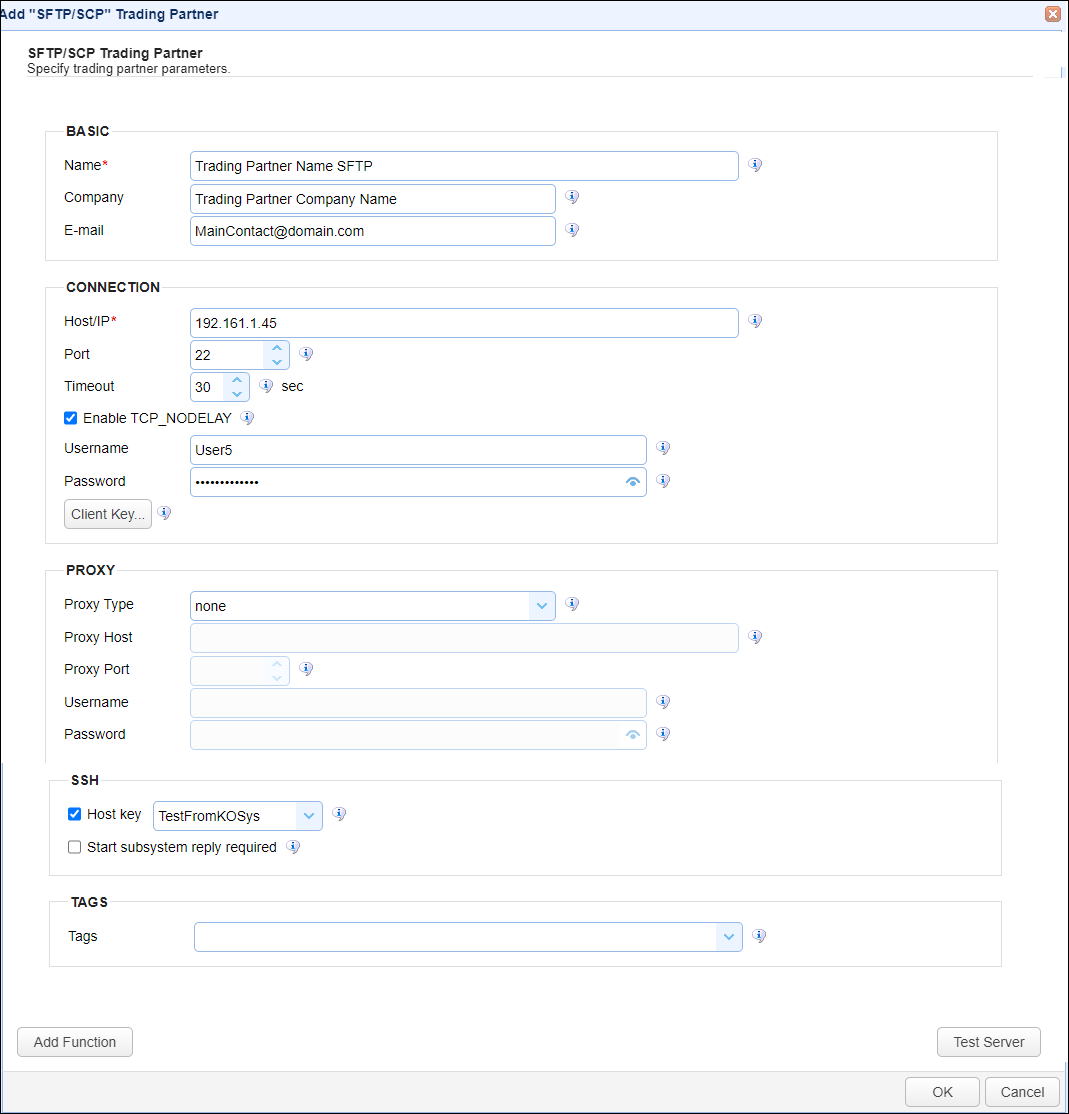
Basic
Name - The unique name to assign to this trading partner. Enter a name that best describes the trading partner, as you will be selecting the name when using the partner in MFT Server features that support it.
Company - The name of the company that this trading partner represents.
E-mail - The primary email address for this trading partner.
Connection
Host/IP - The hostname or IP address for the remote SFTP or SCP service.
Port - The port number for the remote SFTP or SCP service.
Timeout - The maximum time (in seconds) for establishing a connection to the remote SFTP or SCP service.
Enable TCP_NODELAY - If checked, this setting disables Nagle's algorithm.
Username - The username when logging in to the remote SFTP or SCP service.
Password - The password when logging in to the remote SFTP or SCP service. How the remote service is configured will determine if a password is required.
Client Key - When configured, SSH public key authentication is being used to enhance the authentication of the MFT Server (the client) connection to the remote SFTP or SCP service. If the remote service is configured to use SSH public key authentication, click the Client Key button, then select the client key type, which consists of the two options below. Note: The remote service administrator and the MFT Server administrator are both capable of generating the key pair and providing the appropriate key to the respective party.
| • | Use server key - If selected, you will be provided with a dropdown list of Server Keys to choose from - managed by the Key Manager. Typically this option is selected when the MFT Server administrator provides the public key to the remote service administrator. Choosing this option saves time by allowing you to select an already existing SSH key pair. The public key for the Server Key selected can be exported and sent to the remote service administrator. |
| • | Use key file - If selected, this is a file-based key that must be accessible to the MFT Server For example, C:\PrivateKeyFolder\TradingPartner.prv. Typically this option is selected when the key is already generated by some other application. |
| o | Key file password - If Use key file type is selected, a password may be required if one has been configured by the remote service. |
Proxy
This section is for MFT Server customers who have configured a proxy server that the trading partner connection is required to go through.
Proxy Type - The type of proxy service. The options available are in the drop down list.
| • | Proxy Host - The hostname or IP of the proxy service. |
| • | Proxy Port - The port number of the proxy service. |
| • | Username - The username used when logging in to the proxy service. |
| • | Password - The password used when logging in to the proxy service. |
SSH
Host Key - If checked, this means SSH public key authentication is being used to verify the identity of the remote server. The field's dropdown list allows you to select a Host key - managed by the Key Manager. The Host key is the public key of an SSH key pair generated by the administrator of the remote service, then sent to the MFT Server administrator. The public key can then be imported into the Host Keys grid - on the global-level (Keys > Host Keys) or domain-level (SECURITY > Keys > Host Keys). The corresponding private key is stored on the remote service.
Start subsystem reply required - If checked, the start subsystem reply is required.
Tags
Tags - If specified, this is the one or more tags that are used to limit which administrators have access to this trading partner.
Example using the SFTP/SCP trading partner in a trigger action
Triggers are created on the domain-level in AUTOMATION > Triggers. Triggers listen for events (e.g., a file download) and respond with automated actions. There are many trading partner-specific trigger actions.This example does not provide all the steps when creating a trigger; it describes how a trigger action would be configured using the SFTP/SCP trading partner. For a complete discussion about triggers, click here.
Assume, when a trigger event occurs, you would like a file to be automatically uploaded to the SFTP/SCP trading partner.
To accomplish this, you would need to add an action to the trigger, in the Trigger Actions area. The action to add is Trading Partner File Upload as depicted in figure 459 below.
Figure 459
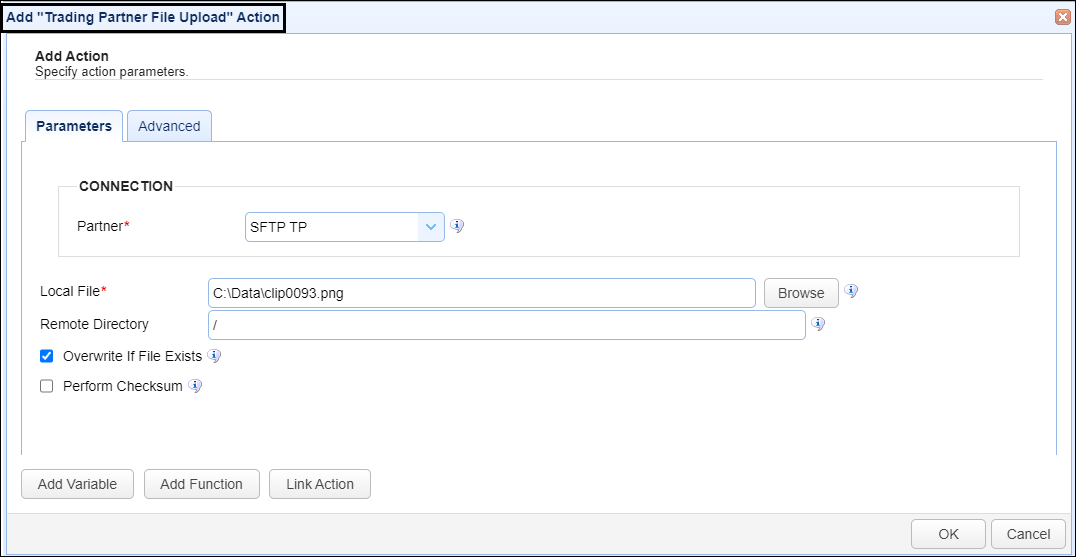
Partner - This is the SFTP/SCP trading partner name. A list of existing trading partners will appear in the dropdown list for you to choose from.
Local File - This is the local file on the MFT Server to upload to the SFTP/SCP remote service.
Remote Directory - This is the directory name that identifies where to upload the file to on the remote SFTP/SCP server. In this example, the home directory for the connecting user (User5 as depicted in figure 458) will be used.