Administrative access may be restricted by client IP. This is recommended in high security environments where administrators may connect only from known client IP addresses. By default MFT Server allows administrators to connect from ANY client IP address.
Figure 107
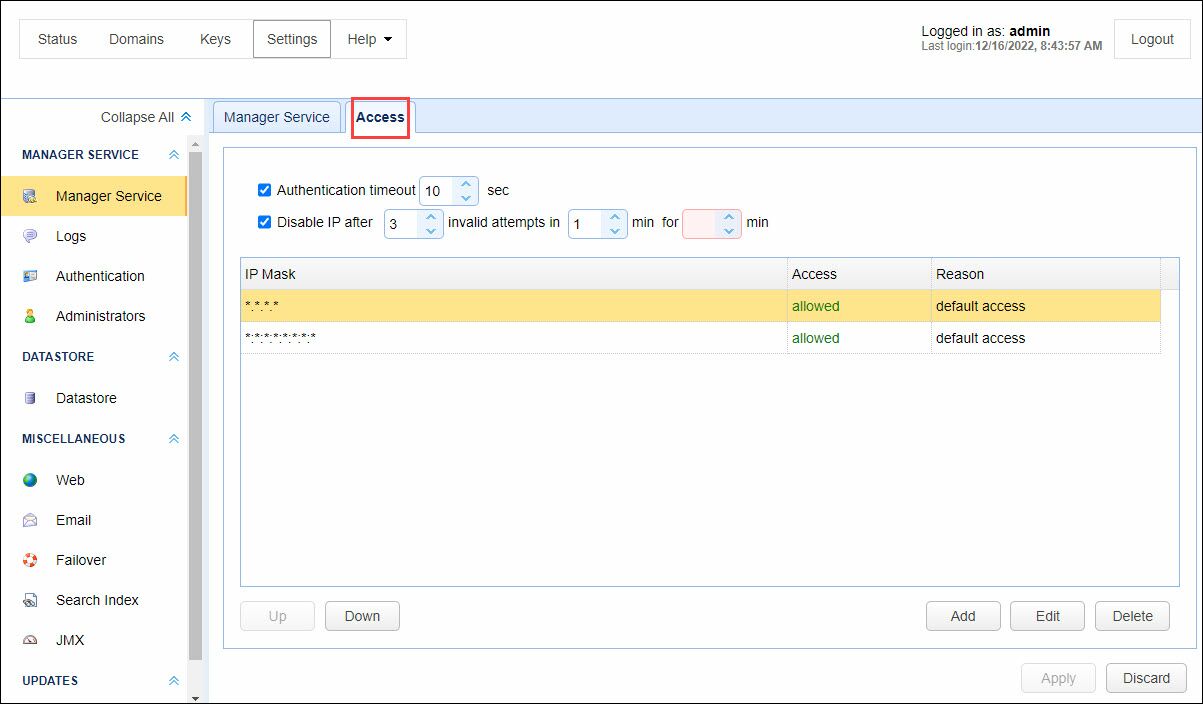
Authentication timeout - The amount of time in seconds that administrative service client may remain connected without authenticating.
Disable IP after - Disables a client IP address after X invalid authentication attempts within Y minutes for Z minutes. See the Note below.
As an improved security measure you may define what IP addresses are allowed or disallowed access to access the administrative service.
Note: When you allow specific IP address(s), and the "Disable IP after" option is enabled, the allowed IP(s) will not be disabled if too many invalid attempts occur, because they will bypass the Disable rule. The allowed IP(s) take precedence over the rule. In this scenario, you will still see a record in the Access grid stating there were too many invalid authentication attempts, but no action will be taken to block the IP. Always make sure any allowed IP's are trusted.
Examples of valid IP masks are as follows:
192.168.1.1 - Allows/Blocks a single IP address
192.168.1.* - Allows/Blocks all IP addresses in a class C IP block.
192.168.*.* - Allows/Blocks all IP addresses in a class B IP block.
*.*.*.* - Allows/Blocks all IP addresses.